Security Assessments and Response Plan for Bank
| ✅ Paper Type: Free Essay | ✅ Subject: Security |
| ✅ Wordcount: 4928 words | ✅ Published: 18 May 2020 |
SECURITY ASSESSMENT AND RESPONSE PLAN FOR THE UNIVERSITY BANK HEADQUARTERS COMPLEX (UBHQ)
Introduction
Purpose
Risk Management is the systematic process of identifying, analyzing, and responding to likely security risks. It includes maximizing the probability and consequences of positive events and minimizing the probability and consequences of adverse events to the organization’s objectives.
This document encompasses the plan of action for security incidents at the University Bank Headquarters Complex (UBHQ) located at 406 Eglin Pkwy NE, Fort Walton Beach, FL 32548. This plan outlines roles and responsibilities of participating plan personnel, the definition and characterization of security incidents, this plan’s relationships to other UBHQ policies or procedures, and required reporting. The goal of this Security Response Plan is the detection and response to any security incident, ascertain the scope and risk of the incident, respond properly to the incident, disseminate the risks and results to all partners, and to reduce the possibility of the incident reoccurring.
Scope
This plan shall apply to the University Bank Headquarters Complex location at 406 Eglin Pkwy NE, Fort Walton Beach, FL 32548, the networks of the UBHQ, and any personnel who gain access to the complex, its informational systems, or its data.
Maintenance
The UBHQ Corporate Security Office (CSO) shall be responsible for maintaining and revising of this plan document.
Authority
The CSO is entrusted with the execution of this plan in the interest of its original authority.
Relationship to Other Groups at UBHQ
The CSO acts as a representative of the entire University Bank community and will ask for the assistance and cooperation of other departments and personnel as required. The CSO works closely with University Bank Administration, such as Human Resources and the Office of General Counsel for investigational affairs and may assist Law Enforcement entities.
Definitions
Event
An event is any deviation from the normal operations of University Bank’s services, systems, or infrastructure. All incidents are events but not all events are incidents.
Incident
An incident is an event that, as determined by CSO staff, conflicts with this Security Response Plan; an Information Security Policy; other University Bank policy or standard; poses a threat to the UBHQ Infrastructure; or threatens the integrity, confidentiality, or availability of UBHQ Services. Incidents will be determined by reviewing of a variety of sources including CSO monitoring systems, reporting from UBHQ personnel or external entities and interruptions in Service. The CSO uses a variety of tools to evaluate the UBHQ environment and, depending on seriousness or scope of the discovered vulnerability, may warn the affected personnel and departments, or enact other mitigation.
Personally Identifiable Information (PII)
In respect to Security Response, PII is defined as a person’s first name (or first initial) and their last name in combination with one or more of the following:
• Social security number
• Driver’s license number
• A State issued identification card number
• Financial account number with the associated security code or password that would allow access to the account
• Medical or health insurance information
Risk Assessment
Activities undertaken in order to identify potential risks and unsafe conditions inherent in the organization or within targeted systems or processes.
Roles and Responsibilities
Incident Response Coordinator
The CSO employee responsible for collecting all pertinent data of an incident, communicating with appropriate entities, ensuring information completeness, and reporting incident status during and after the investigation.
Incident Response Handlers
Incident Response Handlers are personnel of the CSO, other UBHQ staff, or outside contractors who collect, preserve and evaluate evidence to bring an incident to a conclusion.
Insider Threats
According to CERT [0], insiders are current or former employees, contractors, or business partners who have access to an organization’s restricted data and may use their access to threaten the confidentiality, integrity or availability of an organization’s information or systems. This particular threat is defined because it requires special organizational and technical amendments to the Incident Response Plan as detailed below.
Law Enforcement
Law Enforcement includes the UBHQ Corporate Security Office (CSO), Fort Walton Beach Police Department (FWBPD), federal and state law enforcement agencies, and U.S. government agencies. Interactions with these groups will be coordinated with the University Bank Office of General Counsel.
University Bank Office of General Counsel (UBOGC)[1]
University Bank’s Office of General Counsel (UBOGC) is the liaison between the CSO and outside Law Enforcement and provides counsel on all disclosures to law enforcement and the public.
Officers
Officers are personnel selected for various regulatory functions to which University Bank is required to comply.
Users
Users are UBHQ personnel or anyone accessing UBHQ networks, Information Systems, or Institutional Data who may be affected by an incident.
Methodology
This Incident Response Plan outlines some general guidelines and will be complemented by specific internal guidelines and procedures that describe the use of UBHQ security systems and/or methods of communication. These internal guidelines and procedures are subject to amendment as technologies changs. It is assumed that these guidelines will be documented in detail and kept up-to-date.
Constituencies
The CSO represents the entire UBHQ Complex, its Information System and Institutional Data. Some departments and branches may maintain their own Security staffs and some branches of University Bank are located in other cities or countries. To the extent possible, the CSO will attempt to coordinate its efforts with these other groups and to represent University Bank’s security posture and activities.
Evidence Preservation
The goal of this plan is to reduce and contain the scope of an incident, ensure that all assets are protected, and that business and services return to operation as quickly as possible. While rapid response is essential, the CSO balances that speed with requirements to abide by legal and administrative requirements for documentation and chain of custody, and to collect and preserve evidence in a manner consistent with the requirements of rules 26-34 of the Federal Rules of Civil Discovery [2].
Operational Level Agreements
University Bank has operational level agreements with the customers they serve. Any interruption in service is a hardship and the CSO will cooperate with these groups to ensure that service downtime is minimized. However, the CSO’s management supports the prioritization of investigation activities where there is significant risk, and this may result in temporary outages or interruptions.
Risk Assessments
Using various tools, the CSO assessed the physical security risk of the University Bank Headquarters Complex (UBHQ) located at 406 Eglin Pkwy NE, Fort Walton Beach, FL 32548. These included law enforcement crime data available on the geographic location of UBHQ. The CSO had access to spreadsheets and reports, as well as conducted talks the FWBPD to ascertain the types of crime they’re seeing in the area and what the response times are like for that department when a crime is reported. Commercial reports such as the CAP Index were used to augment law enforcement reports. Crime reports of University Bank peers in the area were also evaluated, including information about what equipment and procedures worked, and what didn’t.
A physical walkthrough and an IT audit were performed to assess the scope, vulnerabilities, and security requirements of the UBHQ Complex. These including conducting physical penetration tests, interviewing personnel on knowledge of policies and procedures, and performing social engineering tests to gain access to the building and data servers, and the use of phishing emails to gain access to information.
Staffing for an Incident Response Capability
The CSO will maintain sufficient staffing (including third-party involvement) to investigate each incident to completion and communicate its status to other parties while it monitors the tools that detect new events. Insufficient staffing will impact rapid response capability and resiliency, as will degradation of the tools used for detection, monitoring, and response.
Training
The continuous improvement of incident handling processes implies that those processes are periodically reviewed, tested and translated into recommendations for improvements. UBHQ staff inside and outside of the CSO will periodically train on procedures for handling and reporting incidents to ensure that there is a consistent and appropriate response to incidents, and that post-incident findings are incorporated into procedural improvements.
Incident Response Phases
The basics of the incident process consists of six phases: preparation, detection, containment, investigation, remediation and recovery. The relationship between these phases is emphasized in Figure 1. These phases are defined in NIST SP 800-61 (Computer Security Incident Handling Guide) [3].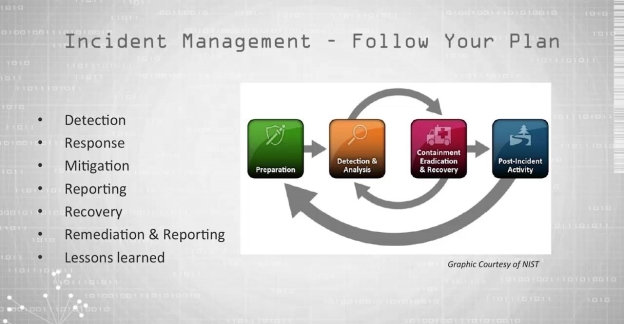
Figure 1: The NIST Incident Response Life Cycle (Cichonski, Millar, Grance, & Scarfone, 2012)
Preparation
Preparations are the activities that allow the CSO to respond to an incident. These may be policies, procedures, plans, tools, and communications. This implies that the affected departments and personnel have established the controls necessary to recover and continue normal operations after an incident. Historical analysis of previous incidents should form a basis for continuous improvement.
Detection
Detection is the discovery of an event using security tools, or information from internal or external sources about a suspected or potential incident. This includes declaring and initial characterization of the incident.
Containment
In this phase, the affected department(s) or entities are identified, isolated or otherwise mitigated. Affected entities are notified and the investigative status established.
Investigation
Investigation is when CSO personnel determine the scope, priority, and cause of the incident.
Remediation
Remediation is the repair of affected departments, systems, and communications after the incident. The determination of reporting requirements, and to whom, will be made in cooperation with UBOGC.
Recovery
Recovery is the analysis of the incident for its implications to policies and procedures, the gathering of data, and the incorporation of lessons learned into future response and training.
Special Guidelines for the Incident Response Process
This section provides guidelines for addressing common issues when responding to an incident. The Incident Response Coordinator, Director of Information Security and Office of General Counsel should be consulted for questions and incident types not covered by these guidelines.
Insider Threats
In the case that a particular Incident Response Handler is a person of interest in an incident, the Incident Response Coordinator will assign other Incident Response Handlers to the incident. In the case that the Incident Response Coordinator is a person of interest in an incident, the Director of Information Security will act in their stead or appoint a designee to act on their behalf. In the case that the Director of Information Security is a person of interest in an incident, the Chief Information Officer (CIO) will act in their stead or appoint a designee to act on their behalf. In the case that another UBHQ administrative authority is a person of interest in an incident, the CSO will work with the remaining administrative authorities in the CSO’s reporting line to designate a particular point of contact or protocol for communications.
Interactions with Law Enforcement
With approximately 85 percent of the critical infrastructure of the United States being owned by the private sector, collaboration between local law enforcement and the private security sector is essential to providing effective security services and to protect these assets [4]. All communications with external law enforcement entities are made after consultation with the UBOGC. The CSO works with the FWBPD, where authorized by UBOGC, to determine the information sharing requirements and shares the minimum information necessary for incident response effectiveness.
Communications Plan
All communication about an incident to external entities outside of UBHQ are made only after consultating with UBOGC. The minimum information necessary to share for an incident is determined by the Incident Response Coordinator and the Director of Information Security in consultation with UBOGC or UBHQ Administration.
Privacy
The Privacy Policy provides specific requirements for maintaining the privacy of University Bank associates and customers. All incident response procedures will follow the current privacy requirements as set out in the Privacy Policy. Exceptions must be approved by UBOGC.
Documentation, Tracking and Reporting
Incident response activities shall be documented to include information obtained using methods consistent with chain of custody and confidentiality requirements. Incidents will be prioritized and ranked according to their potential for disclosing sensitive data. As an investigation progresses, that ranking may change, resulting in a greater or lesser prioritization of CSO resources.
Incidents will be reviewed to assess whether the investigational process was successful and effective. Subsequent adjustments may be made to methods and procedures used by the CSO and by other participants to improve the incident response process.
Security Assessment
(See page 9 for Methodologies used)
Physical Security
- Intrusion Detection Systems (IDS) – Audible alarms are discernable. Alarm displays are clearly visible and identify the location and type of alarm, and the operator interface allows for alarm recognition by the operator. Alarm communication lines and other detection devices have continuous supervision to preclude any covert attempt to bypass the alarm system, and to ensure an appropriate and timely response. Facility management has provided for adequate equipment, an effective testing and maintenance program, and a sufficient number of trained personnel to operate the alarm and assessment equipment. Exterior systems are be capable of withstanding the environmental conditions of FWB.
The exterior system uses two or more types of complementary sensors, including fixed-position CCTV coverage, a fence disturbance system, and motion sensors.
The interior systems are designed, installed, and maintained in a manner to eliminate gaps in detection coverage and to prohibit adversaries from circumventing the detection system. It consists of passive infrared, video motion detection, and disturbance detection.
CCTV systems are used in conjunction with alarm and detection systems and can automatically call the operator’s attention to an alarm-associated camera display, and the camera’s picture quality, field of view, and image size is such that the operator can easily recognize human presence. Video recorders used with the CCTV system operate automatically and are rapid enough to accurately record an intrusion. See Figure 2 for IDS layout.
An auxiliary power source consisting of an uninterruptible power supply (UPS) and generator is available, and switchover is immediate and automatic if the primary power source fails.
Protection systems include a suitable means of assessing alarms and provide for an appropriate response. The CSO is responsible for monitoring the IDS and responding to IDS alarms.
Effective lighting provides a deterrent to adversary intrusion, and also assists the CSO in locating and assessing alarm initiations and provides for effective use of CCTV as a surveillance and assessment tool. Lights have a minimum specified luminescence at ground level for specific areas, a regular power source, and an emergency backup lighting capability. Lights do not cause glare or bright spots in CCTV camera images.
Common Deficiencies/Potential Concerns
- False and Nuisance Alarms
- Improper Installation, Calibration, or Alignment
- Inadequate Testing and Maintenance Program
- Failure to Properly Assess and Respond
Recommendations
- Tamper Protection for IDS Enclosures, Junction Boxes, and Power Sources
- Efficient and annual training of personnel in recognition, response, training and maintenance of systems

Figure 2.
- Entry and Search Control – A security badge system is used to ensure that only authorized personnel enter, occupy, or leave a security area, and to indicate the limitations placed on access to classified matter. A CCTV identification system is used in conjunction with protection personnel stationed at the entry point to provide positive identification of personnel entering security areas. Card readers are used to supplement badge checks as a means of access control. These devices control access to inner security areas and at facility entry and exit portals. Door locks opened by card readers relock after the door has closed to prevent a person from immediately opening the door while it is still in the unlock mode. Guards at entrances and exits randomly check briefcases, boxes or portable PCs to prevent unauthorized items from coming in or leaving. Metal detectors are used for searching personnel to ensure that explosive components, weapons, or other prohibited metal articles are not introduced without authorization. CSO personnel are trained for clearing alarms and for taking appropriate actions when a violation is identified. Backup detectors (hand-held) are available at each location where metal detector portals are in use to resolve portal alarms and for use in the event of portal failure.
Common Deficiencies/Potential Concerns
- Inadequate Monitoring
- CCTV Systems vulnerable to disguise and false credentials
- Card Reader Systems verify the coded badge or credential, not the identity of a person, and are also vulnerable to counterfeiting and decoding
- Metal that is passed through the detector very slowly or rapidly may not be detected
Recommendations
- Personnel assigned to monitor activity must be properly trained and sufficiently diligent
- Biometric identifiers to verify personal identity on the basis of a unique physical characteristic, such as eye-retinal pattern, hand geometry, voice, facial recognition, or fingerprints.
- Badging – UBHQ utilizes computer-generated badges that have a magnetic stripe coded for access control. The UBHQ employment department handles badge issuing functions.
Common Deficiencies/Potential Concerns
- Improper Badge Accountability Procedures. Records documenting the disposition of all badges may lack the required information.
- Improper Storage of Unused Badging Materials and Unissued Badges
- Badges of terminated employees are not always promptly recovered
- Improper Badge Destruction
- Failure to Update Badge Photos
- Incomplete Handling of Lost Badges
- Insufficient Understanding of Policies and Procedures for All Issued Badges
Recommendations
- SPO issuance and control of badges
- Consider a centralized badge office, with a number of satellite activities that perform the badging functions.
- Ensure understanding of policies and procedures for all types of badges.
- Barriers – Physical barriers control, impede, or deny access and effectively direct the flow of personnel and vehicles through designated portals. Fencing encloses security areas and designates UBHQ property boundaries. Fences have regular patrols, continuous observation, and an IDS supported by alarm assessment equipment. Building materials are solid and offer penetration resistance to, and evidence of, unauthorized entry. Windows are constructed of shatter-resistant, laminated glass and installed in fixed frames so that the panes are not removable from the outside. Window frames are securely anchored in the walls and lock from the inside. Vehicle barriers of cables and bollards are used to deter penetration into security areas.
Common Deficiencies/Potential Concerns
- Erosion of the ground under the fence can produce gaps or washouts that may allow someone to crawl under the fence. Another common problem is that vegetation is allowed to grow up close to the fence, potentially providing concealment for adversaries or a platform for climbing over the fence.
- Vehicle barriers must be effectively monitored, and components must be appropriately located. Barriers should be within an area that is protected by detection sensors.
Recommendations
- SPO issuance and control of badges
- Consider active denial systems, of cold smoke, carbon dioxide, or other dispersible materials such as sticky foam, rigid foam, sprays, and irritant agents. These substances should be properly maintained and protected against tampering.
- Locks and Keys – Locks are used to control, impede, or deny access and to effectively direct the flow of personnel and vehicles through designated portals. Specifically, locks are designed to: reduce the number of entry and exit paths, keep unauthorized personnel from entering areas where they are not allowed, and control access to assets within areas to individuals with an approved need. A strict key control program has been developed, implemented, and effectively managed to ensure continuous accountability of security keys. [x] Access to security keys, key blanks, and key cutting codes is protected.
Common Deficiencies/Potential Concerns
- Lock specifications often do not meet required standards.
- Appropriate procedures for dealing with lost keys must be established.
- Custodians do not maintain an effective accountability system for security keys and allow obsolete or unusable keys to accumulate without taking appropriate destruction action.
Recommendations
- The objective for organization is to reduce the number of keys and move toward a keyless access control technology.
- Verify accountability of 100 percent of traditional keys. Each of these keys must be physically touched by the assessor and its stamped serial number checked.
- Communications – The design of communication systems is such that no single event can disable all modes of communication between the alarm stations and fixed posts or between the alarm stations and CSO or FWBPD. Records of the failure and repair of all communications equipment are maintained in a form suitable for compilation by type of failure, unit serial number, and equipment type. Radios are used for voice communications among members of the CSO and alarm stations, and with UBHQ managers and other participants, when required. Additionally, radios are used to communicate with FWBPD, who participate in exercises or respond to emergencies. To provide the flexibility necessary for all participants who may need radio communication capability during an incident, a number of frequencies are available. the telephone system used for security purposes is protected (alarmed, buried cable in a conduit) and has backup provisions. Duress alarms are used to alert CSO to emergency or duress conditions. The alarm can be activated in an unobtrusive manner and does not annunciate at the post initiating the alarm. These alarms are hardwired devices that are protected from tampering.
Common Deficiencies/Potential Concerns
- Some radio systems used at UBHQ do not have enough channels (radio frequencies) available to provide effective communications for all who need to use the radio.
- The cellular carriers that are used for alternative communications are not evaluated for vulnerabilities.
Recommendations
- Consider employing encrypted radios.
- Install repeaters to increase radio communications range and clarity, especially through the thick concrete of the parking structure, and protect these devices (antennas and other exterior components) from tampering and sabotage.
- Evaluate cellular carrier’s vulnerabilities. Restrict personal cell phone usage on-site.


Information Security
- Security Information Management Systems – Web services and information they can delivery are desirable targets for misuse. [m] A Security Information Management System is in place and encompasses the features listed below.
- Firewall – A firewall to block unauthorized requests and pass through only designated traffic, to prevent unscrupulous third parties from exploiting the information on UBHQ computers and systems. [n]
- Anti-virus & Anti-malware – Protection is in place against Trojans, viruses and worms, predictable-yet-still-dangerous malware. [o]
- Web content filtering – Web content filtering is in place to prevent malware exposure, content liabilities, and meets government compliance.
- Encryption – Security solutions are utilized to protect data transfer of sensitive information across devices and systems. [q]
- Electronic Information Access – Access to records is limited to those whose official duties require it. Electronic records are password protected. [r]
- Digital Fraud – Banks have the responsibility to protect customers’ confidential, personally identifiable (PII). [s] A comprehensive data protection plan is in place to safeguard data privacy, lineage, and data control.
Common Deficiencies/Potential Concerns
- Unauthorized disclosure, modification, or destruction of information
- Inadvertent modification or destruction of information
- Nondelivery or misdelivery of service
- Denial or degradation of service
Recommendations
- Periodic review of Security Information Management System to ensure it’s up-to-date.
- Frequent updating of system Anti-virus & Anti-malware protection.
- Effective training and re-training of UBHQ personnel to ensure comprehension of current standards and procedures.
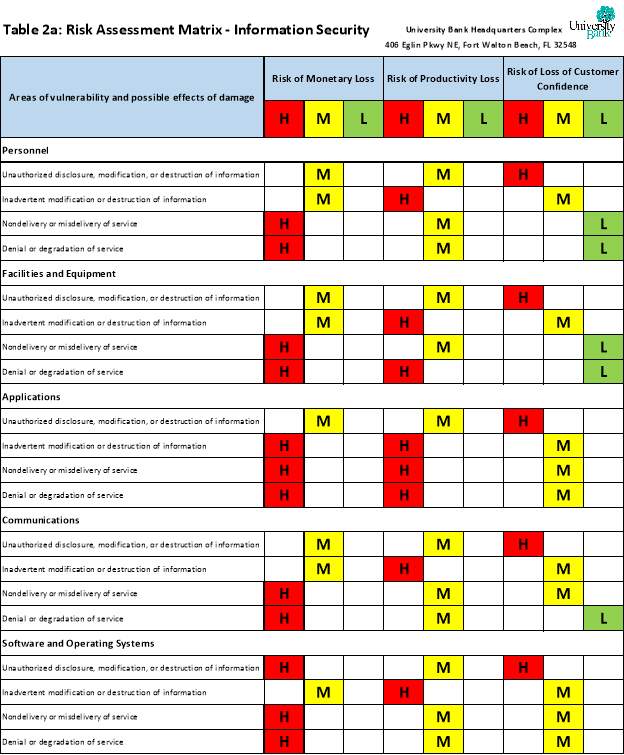

Crime Assessment
- History of local criminal activity. [See Table 3.]

- Location and accessibility to law enforcement and emergency services.
- See Figures 3, 3a, 3b

Figure 3.


Environmental Considerations
Natural disasters, such as hurricanes, are an anticipated threat to anyone doing living or business in Coastal Florida [8]. See Figure 4. Hurricanes can also spawn landslides and tornadoes. The organization needs to ensure business continuity. This should be accomplished by reaching out to its clients before a hurricane strikes, assist them in withdrawing funds to use for emergency purposes, and accessing their accounts through mobile and online banking, and secure all documents and valuables in safety deposit boxes. During recovery, the bank cannot get back to business and serving customers if they don’t know the safety or location of its employees. Each storm is different in how it impacts road safety, building structures, power and connectivity. Thus, the established response plan must remain flexible and have built in redundancy. It should be updated yearly [9].
Care must also be taken to safeguard against those who would seek to exploit the bank’s vulnerability caused by damage to the building structure or IT systems.

Figure 4. [8]
Further Information
Further information on the UBHQ Security Assessment Response Plan and its associated procedures can be obtained from the Incident Response Coordinator of the CSO via csoir@ubhq.co or 800-867-5309.
Revision History
|
Version |
Date |
Author |
Description |
|
1.0 |
19 Oct 2019 |
Adam A. Wade <aawade> |
Initial Document |
References
[Figure 3] Google (n.d.). [Google Maps images of 406 Eglin Pkwy NE, Fort Walton Beach, FL 32548]. Retrieved October 19, 2019, from https://www.google.com/maps/place/406+Eglin+Pkwy+NE,+Fort+Walton+Beach,+FL+32547/@30.4371111,-86.6043799,681m/data=!3m2!1e3!4b1!4m5!3m4!1s0x88913f0abda28cbf:0x47755afb9f6655af!8m2!3d30.4371111!4d-86.6021859
[0] Carnegie Mellon University’s Software Engineering Institute. CERT Insider Threat Center. Technical Note. Common Sense Guide to Mitigating Insider Threats, Fifth Edition. Retrieved Oct 2019 from https://www.dni.gov/files/NCSC/documents/nittf/20180209-CERT-Common-Sense-Guide-Fifth-Edition.pdf
[1] U.S. Department of Health & Human Services https://www.hhs.gov/about/agencies/ogc/index.html
[2] RULES OF CIVIL PROCEDURE FOR THE UNITED STATES DISTRICT COURTS. TITLE V. Disclosures and Discovery. Fed. R. Civ. P. 26-34. Retrieved Oct 2019 from https://www.uscourts.gov/sites/default/files/Rules%20of%20Civil%20Procedure.
[3] [Figure 1] P. Cichonski, T. Millar, T. Grance, and K. Scarfone, “Computer Security Incident Handling Guide,” Technical report, SP 800-61 Rev. 2, Gaithersburg, MD, United States, 2012. (Online) Available at https://csrc.nist.gov/publications/detail/sp/800-61/rev-2/final
[4] U.S Government Accountability Office Report. (2006) Critical Infrastructure Protection: Progress Coordinating Government and Private Sector Efforts Varies by Sectors’ Characteristics. (Online) Available at https://www.gao.gov/assets/260/252603.pdf
[7] [a] Vellani, K. H. (2007). Strategic Security Management: A Risk Assessment Guide for Decision Makers. Amsterdam: Butterworth-Heinemann. Retrieved from https://search-ebscohost-com.libauth.purdueglobal.edu/login.aspx?direct=true&db=nlebk&AN=182187&site=eds-live
[8] The Florida Center for Instructional Technology. FL Maps>Hurricanes and Tropical Storms> Storms by Decade. Information compiled and retrieved Oct 2019 from https://fcit.usf.edu/florida/maps/galleries/hurricanesandtropicalstorms/stormsbydecade/index.php
[9] Federal Deposit Insurance Corporation (FDIC). FDIC Outlook – Winter 2005. A Preliminary Assessment of the Effects of Recent Hurricanes on FDIC-Insured Institutions. (Online) Available at https://www.fdic.gov/bank/analytical/regional/t4q2005.pdf
[a] U.S Government Accountability Office Report. (2006) Critical Infrastructure Protection: Progress Coordinating Government and Private Sector Efforts Varies by Sectors’ Characteristics. (Online) Available at https://www.gao.gov/assets/260/252603.pdf
[b] Pancake, D. (1983). The New Professionals: Cooperation between Police Departments and Private Security, Police Chief.
[c] Bureau of Justice Assistance, Engaging the Private Sector to Promote Homeland Security: Law Enforcement-Private Security Partnerships (2005). Available at https://www.ncjrs.gov/pdffiles1/bja/210678.pdf
[d] Burdeau v. McDowell, 256 U.S. 465 (1921). https://1-next-westlaw-com.libauth.purdueglobal.edu/Link/Document/FullText?findType=Y&serNum=1921113668&pubNum=0000780&transitionType=Default&contextData=%28sc.Default%29
[e] Birkner v. Salt Lake County, 771 P.2d 1053 (Utah 1989). https://law.justia.com/cases/utah/supreme-court/1989/19966.html
[f] 42 USC §1983. Civil action for deprivation of rights. Retrieved from https://1-next-westlaw-com.libauth.purdueglobal.edu/Document/NDFE80F60AFF711D8803AE0632FEDDFBF/View/FullText.html
[g] Frankel, R. (2009). Regulating privatized government through § 1983. The University of Chicago Law Review, 76(4), 1449-1515. Retrieved from https://libauth.purdueglobal.edu/login?url=https://search-proquest-com.libauth.purdueglobal.edu/docview/214786639?accountid=34544
[h] Parent, D., Snyder, B. (1999) U.S. Department of Justice. National Institute of Justice. Issues and Practices in Criminal Justice. Police-Corrections Partnership https://www.ncjrs.gov/pdffiles1/175047.pdf
[i] Waugh, W.L., Streib, G. (2006) Public Administration Review. Collaboration and Leadership for Effective Emergency Management. Georgia State University. (Online) Available at http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.461.2066&rep=rep1&type=pdf
[j] Florida Statutes (2016) Title 32. Regulation of Professions and Occupations. Chapter 493. Private Investigative, Private Security, and Repossession Services. General Provisions. Retrieved Oct 2019 from http://flsenate.gov/Laws/Statutes/2016/Chapter493
Nemeth, Charles. Private Security and the Law, Fourth Edition. 4 ed. Boston: Butterworth-Heinemann, 2011. (Online) Available at https://www.selfdefensefund.com/wp-content/uploads/2017/09/Private-Security.pdf
[m] Mitropoulos, S., Patsos, D., & Douligeris, C. (2007). Incident response requirements for distributed security information management systems. Information Management & Computer Security, 15(3), 226. http://dx.doi.org.libauth.purdueglobal.edu/10.1108/09685220710759568
[n] Information Services & Technology (IS&T) at Boston University. How Firewalls Work (Online article) Available athttps://www.bu.edu/tech/about/security-resources/host-based/intro/
[o] The difference between antivirus and anti-malware. (2016, May 17). The Spectrum Retrieved from https://libauth.purdueglobal.edu/login?url=https://search-proquest-com.libauth.purdueglobal.edu/docview/1789212133?accountid=34544
[q] Encryption software (disk encryption, File/Folder encryption, database encryption, communication encryption, cloud encryption) market 2015 – 2019. (2015, Feb 10). PR Newswire Europe Including UK Disclose Retrieved from https://libauth.purdueglobal.edu/login?url=https://search-proquest-com.libauth.purdueglobal.edu/docview/1652772841?accountid=34544
[r] Board of Governors of the Federal Reserve System – FRB – Personnel Security Systems (Online) Available at https://www.federalreserve.gov/files/BGFRS-2-personnel-security-systems.pdf
[s] Digital fraud: 5 ways lenders can safeguard customer information. (2019). Dataquest, Retrieved from https://libauth.purdueglobal.edu/login?url=https://search-proquest-com.libauth.purdueglobal.edu/docview/2180689615?accountid=34544
[x] The officially designated security authority (ODSA) must establish a program to protect and manage locks and keys, and the requirements for security locks must be applied in a graded manner. Locks used to protect classified matter and Category I and II SNM in GSA-approved security containers, vaults, or vault-type rooms must meet Federal specifications (see Federal Specification FF-L-2740A Amendment 1, Locks, Combination). Key locksets Physical Security Systems Assessment Guide – December 2016 PSS-51 must meet American National Standards Institute (ANSI) Standard A156.2-1996, Grade 1, Bored and Preassembled Locks and Latches, or ANSI A156.13-1996, Grade 1, Mortise Locksets. DOE Order 473.3A provides other specific requirements for these locksets.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal



