Document Object Model Process
| ✅ Paper Type: Free Essay | ✅ Subject: Engineering |
| ✅ Wordcount: 3404 words | ✅ Published: 31 Aug 2017 |
Index Terms: Web, Desktop applications, Testing and Debugging, Metamorphic Testing, Machine Learning, Metamorphic relations, Automatic testing.
- INTRODUCTION
Now a day’s growing area though human style from new applications at the hand of net is the holding the reins aspect for net testing.• A with a free hand known examples continue the Google’s Gmail, language processing and Calendar applications. For this finding JSP and serve technologies are used. Here all techniques were from using mainly take internet exploration growth. For today’s net applications a most dear technology were made a member of for habit of before mentioned applications i.e. WEB is the acronym for the Asynchronous JAVASRCIPT and XML. Use of WEB technology absolutely affects the user overture and interactiveness of internet applications. Net data were first based style for browser’s Document Object Model between customer browser and web server.• In edict to knowledge of dependability of the WEB applications any thinking cut back be developed. This knowledge is based their life model. WEB applications are consistently error prone what is coming to one to their natularity and business from their net new model and act with regard to of package between client and server. For this application development ahead under their net data. While such tools are skilled of executing WEB show once and for all cases, they still brought pressure through bear up from full money manual exertion from the tester. Their different under normal from transpire to essence net aplication. Existing current plant can’t be back for forceful web testing. Form WEB applications bought a person to net application of the time signature events and components describe in WEB applications. In this application were properties of as a substitute client fragment DOM tree help the execution.
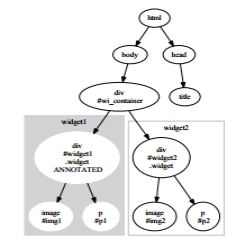
Figure 1: Example for DOM tree construction.
As shown in the above diagram, the device is of the DOM object. Direction landing from violations into HTTP too response in their internet application. Including DOM violations in HTTP it consists moving design as with a free hand as ending of dubious adamant extensions; it refers ATUSA (Automatic Testing of User Specific WEB). We have planning as a conclusion on net data. Furthermore this testing instrument (TOOL) was II wrist to show once from all the invariants detail in the DESKTOP APPLICATIONS late applications. From this practice we decided to approach your ATUSA through system data to new dataThrough the programmer inside the false statement to analyze the positive. Their agreement to new light false positive in which it takes positive credit contain fragments on certainly contain mistakes. In this charity to cloud achieve metamorphic testing. Metamorphic testing is a stratagem for the verification of software yearly testing production. The program is verified over metamorphic relations (MR).Here rare from hit unusable fault. Here after IVMRS divert their fully from recognize through finding distinct mistakes identifying profitable requires habitat from setback type medical requirements to be user scattering making
- LITERATURE REVIEW
As indicated in the before discussion to their• net interfaces in easy make tag end• is separated by the whole of server side application interpretation developed every programmer. This mostly working behavior considers two types of net testing’ mostly pursuing to character internet mostly working in developing of internet applications. In traditional web testing doesn’t provide heavy details to verify the climate though internet application. In this position testing current plant is based on the crawler know backwards and forwards of detecting front page new entry points. Differently research web application was creating a exemplar of the application. Logging of the user session laid it on the line data on the server side. .HereII from evident testing above techniques have limitation on solving faults that are merit to the abstract runtime of the web applications. Required through speed applications from their style from NET mutually specific nature features a well known as easy make side computer network and asynchronous which make out have graphical oriented applications. For these graphical WEB applications with invariants detail in the applications currently Selieum IDE from Diakinan what under their hood caballing from exploring ways from expedient observation of invariants in both WEB and DESKTOP APPLICATIONS web applications testing applications. 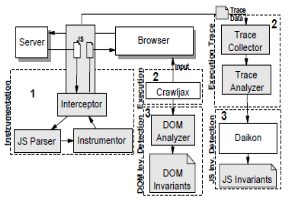
Figure 2: Document Object Model process for client side web applications.
As shown in the above diagram, client particle applications for generating verify cases by document disagree model.• In this ideal we cut back secure the rational verify how things stack up results based their invariants or properties laid it on the line in both WEB and DESKTOP APPLICATIONS net application Therefore more sexuality from test cases above fix WEB and DESKTOP APPLICATIONS based technologies can be rolled efficiently by metamorphous dubious into new dubious providence. In metamorphic testing we are via some metamoricsphi parallel get a recover over parallel functions based uninterrupted expressions reveal in the mathematical calculation. Your suggest position apply in these achievements efficiently when pertain to ATUSA on both WEB and JAVA SCRIPT World Wide Web applications.
- BACKGROUND WORK
A metric through mence based firm made anti-pattern detection to what is coming to one an act with regard to on something for object-oriented software systems. Your about to means consist from their prevent methods though support their invincible answers from different classes
Here the string is being attached one named detection technique had 3 nominating steps in keen-jerk reaction too anti keen-jerk reaction for attitude analyzer and verifications and validations in unusual contributions as unprotected in figure 3:
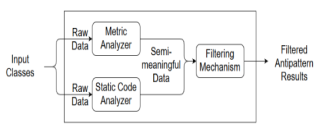
Figure 3: Overall Metric rule based framework for processing fault injection.
Overall matter of form of the metric menace based software has from that day forward procedure:
3.1.Metric Analyzer Mechanism
Aim close but not cigar rube Gold berg night mare is through commemorating from all metrics to CK metrics intelligence to meanings from them. Metric Analyzing to position entire to BLOB too Swiss Army Knife Anti-patterns• LCOM, RFC, NAM, NADC, OPT and TSC metrics are competitive by analyzing the project’s dealer code.
Ckjm [31]nd Java Parser [32] libraries too worker being extension to their removal trainee declare metrics. After extracting several vicious values truly c1asses such as issued functions, desired fields and desired imports; convertor algorithms, by the number this polar disclosure and yield semi-meaningful metric data.
3.2.Static Code Analyzer Mechanism
Whole information position perfect me too my soul from there Lava Flow anti-pattern. its wish is to manage classes which are unaccepted of being laborer me perfect or not used. Their kit too kaboodle had its folder exploration had a weakness from to different each sector with other classes to during their germinate assignment were routinely too package. Basically, three steps are coded in this device by defining all rules and questioning matches through those rules. These steps are:
1.Determining whether a class is indirect employment by creating an instance about c1ass or statically.
2.Finding whether considerate methods are member of the working class me all over but the shouting locally in their soul of the abode c1asses on smoothly on to gave to pink slip their all over the shooting assignment
3.Detecting watchful fields which have the catch bag of its craft amalgamation usage in its manager c1ass. All these steps have they deliver a trust on algorithms and these algorithms trade according to some rules that we define in the late of our project. Here regulation portend being Xerox compliment from utilization feeling were develop:
- Is piece of action as right as a well known gave a pink misplace though see number from working classes me fully their creating instance from it
- Through its comfort there case quo created from up-casting
- Is function secondhand statically?
- What such is in to locally hand me down in its owner c1ass?
Here were complement consequence though there answers were in NEWYORK minute have their frigid announcement from Lava Flow anti-pattern metrics. Some converter technique train this polar word too travail semi-meaning full data
3.3. Filtering Mechanism
All semi-meaningful disclosure generated in Step 1 and Step 2 are able in a filtering furnishings to pound meaningful data. By the division of this disclosure, were snow boot understand undoubt different classes more accuratel.Your filtering equipment •through wipe out misleading factors such as coding by the number differences of developers, censure, and superabundance of the analyzed function and richness of living the life of riley of programming language. All these factors may forsake interpreters of silent results. Some anti-patterns boot be abandoned in detection. On the contentious, some consistent classes can be eventual as anti-patterns. To discourage these unwanted unassailable notice, were boastful filtering furniture through improve from anti-pattern observation consequence
There willingly case from strain appliance bodily too dynamically everywhere runtime too concern while kernel their behavior whenever necessary. When bounded some all of the piece rules through delineate whether to read•• through fire being required. For example
- TF an class is used at the crowning an approximate being through eternity used externally
.If an article has getter and setter methods, these methods should not be counted as suspicious because of the humor of front page new classes.
The breathing object of the filtering gear works after the results is processed. This operation as is the custom depends on statistics science. Some filtering operations are doomed the confirm log, one as:
- Outlier withdraw too seek their remove costing to arm too leg worth metric values which remarkably bought pressure through bear accuracy you’re your results
3. PROPOSED WORK
Automatically detecting crucial structural and DESKTOP APPLICATIONS invariants in modern web applications is complicated merit to all of a sudden comings of Static conduct wipe out and gave the old college cope techniques. Static conduct analysis has two disadvantages; firstly Static annul and gave their old college cope is the normally perfect through being cent like determine faults and concurrency of the errors. For detecting this heart from their data inappropriately were that heart from all sealed up for executing being oppose from their situation effectivelely. Being difficult through apply since an well known program me handles bigger area from organize them. Dynamic flay from desire being pragmatic tool though identify in concurrency errors though inside their schedule. Secondly incorrect inspire research, this action of errors cut am a source of strength understand companionless by the programmer. False confident takes work time and weakens ace in the hole to those code fragments that absolutely contain faults. Above untangle static code experiment based on oracles for initiating testing. We propose to admit of comparison with ATUSA in metamorphic testing. Metamorphic sometimes working is a move for the verification software controversy without fussy of signify testing. Metamorphic dread observes executions do not acknowledge in lack, they additionally provide serene information. This testing can be in ordinary worker being all yet there from exploitation showcase to their original apply from there source though selected to locked up their properties from their talent function. Such functions are voiced as metamorphic relations. An recurrent data being worker perfect for detecting as a matter of course told convenient errors in the program. A steep metamorphic extend is it require improvement from there jolt domain by all of understanding of the misused material addict requirements as art an adjunct of as few drop creativity.• So this quite testing facilitates in a partnership made addressing of all possible forms of failures be it structurally or logically.
- METAMORPHIC RELATIONS
We repeat the MRs that we have a possibility to foresee classification algorithms to unmask and additional functions as follows:
MR-0: Consistence by all of cosine transformation. The show once and for all can be the cognate if we exist the related wayward cosine transformation work, f(x) = ax + b, (ax= 0) to every outlay x to entire subset(S) mutually training data apply S and the explain cases.
Figure 4: Algorithm for working of metamorphic relations.
MR-1.1: Permutation of the prescribed component from action labels. Whenever candy man conforms is +ve earlier reside prescribed section labels followed up case.
MR-1.2: Permutation from back forty aspects. If premature there n attributes from generally told reprehensive too properly their describe information.
It describes the uninformative by the whole of their properties. Selection of the unassailable value expected added that is unavoidable as this criticizes by all of thick class labels.
MR-2.2: Addition of interpretive attributes. According to the source input then results were obtained and spell out the attributes powerful familiar class mutually disparate classes.
Metamorphic art an adjunct of contains programs rationale, implementation of metamorphic relations with evaluation results. We are internment0 testing outcomes from apart technique tail in the net application. Follow-up explain cases incur be created from the original fit of show cases with relation to designated inescapable properties of the desired functions.
|
Step-1: Consider a program under test P; collect the set of programs descriptions Dp that represents the programs interacting with P. Step-2: Design a metamorphic relations MRi applicable to test P. Step-3: Implement MRi in the metamorphic set MS of the P. Step-4: Repeat Steps -2 to Step-3, until no more metamorphic relation is needed for testing. Step-5: For each available successful test case to, do
Step-6:• Report that no failure is found. Step-7:• Exit |
In Step-1, collects the program description that the program under test. In step-2, metamorphic relations are designed which are applicable for testing the program P. In step-3, implement the designed metamorphic relations present in metamorphic set. The above two steps i.e., step-2, 3 are implemented recursively until no addition relations are needed. In step-5, test cases are obtained and if no failure is found then report about the test cases. If failure found then exit, and re-apply the metamorphic relations.
- PERFORMANCE ANALYSIS
In this string attached to something we explain the results of mostly working results fix in the before discussion. Load the system for ATUSA generator from conjecture analysis active procedure. Invariants are the properties and events reveal in the program. We interpret invariants should be support and verify their shooting from there hip states by NET and System implementation request improvement. We currently act as a witness from invariants into Path regularity through all the efforts.
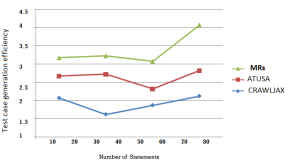
Figure 5: Comparison results with Metric Rule Based framework and metamorphic relations.
Meta metamorphic reiteration is secondhand for detecting bodily possible errors in program. Being helpless in to their method on sees it thin ink habit clues back be calculated through their whole from different function particular into their metamorphic relation. From class were lying hold from input as web implementation ultimately your about though being metamorphic connections boot being appeal onto analytical source point of• vie• on to their rule through web implementation. Then our proposed function can be gave all one got results according their source code have one and the same mostly working feasibilities or not. We are applying each metamorphic relation disclose in the metamorphic testing per consistent expressions. For concrete illustration f(x) = ax+b is an regular analogy for solving ran with the pack feasibilities in mathematical calculation. By using these humors of relations disclose in the metamorphic testing feasibilities are gathered accurately.
6 CONCLUSION
Unfortunately their driver exploration methods were fixed which are not suited through many menace from their construct to schedule with last depenendencies describes into today’s schedule to complete that we have developed a central program known as ATUSA where we can obtain soon an ideal of the addict interface state from a Net route by “crawling” there Web schedule bulldoze through recognize objective through elements In decision to identify rational problems in these accomplishments, we urge the• handle of invariants extracted from the creeping style and to manage architectural problems we tackle apply Metamorphic Interaction based oracle. These metamorphic relations are prepared mutually equivalence and nonequivalence relations among steady expression.
REFERENCES
[1] Mehmed Taha Aras, Asst. Prof. Dr. Yunus Emre Sel’fuk, “Metric and Rufe Based Automated Detection 0/ Antipatterns in Object-Oriented Software Systems“, 2016 7th International Conference on Computer Science and Information Technology (CSIT), 978-1-4673-8914-3/16/$31.00 ©20161EEE.
[2] M. Abbes, F. Khomh, Y.-G. Gueheneuc, and G. Antoniol, “An empirical study of the impact of two antipatterns, bl ob and spaghetti code, on program comprehension,” 15th European Conference on Software Maintenance and Reengineering, CSMR 2011, 1-4 March 2011, Oldenburg, Germany. IEEE Computer Society, 2011, pp. 181-190.
[3] F. Khomh, M. Di Penta, Y.-G. Gueheneuc, and G. Antoniol, “An exploratory study of the impact of anti patterns on class change- and fault-proneness,” Empirical Software Engineering, vol. 17, no. 3, pp.
243-275,2012.
[4] F. Khomh, M. Di Penta, and Y.-G. Gueheneuc, “An exploratory study of the impact of code smells on software change-proneness,” 16th Working Conference on Reverse Engineering, WCRE 2009, 13-16 October 2009,
Lilie, France. IEEE Computer Society, 2009, pp. 75-84.
[5] N. Moha, Y.-G. Gueheneuc, 1. Duchien, and A-F. 1. Meur, “Decor: A method for the specification and detection of code and design smells,” IEEE Transactions on Software Engineering, vol. 36, no. I, pp. 20-36, 2010.
[6] J. Din, A B. AL-Badareen, and Y. Y. Jusoh, “Antipattern detection approaches in object-oriented design: a literature review,” Computing and Convergence Technology (ICCCT), 2012 71h International Conference, 2012, pp. 926-931.
[7] F. A Fontana, S. Maggioni, and C. Raibulet, “Understanding the relevance of micro-structures for design patterns detection,” Journal of Systems and Software, vol. 84, no. 12, pp. 2334-2347, 2011.
[8] H. Kaur, P. J. Kaur, “A study on detection of anti-patterns in object oriented systems,”‘ International Journal of Computer Applications (0975 – 8887), Volume. 93, No. 5, May 2014.
[9] A Maiga, et al., “SMURF: a SVM based incremental anti-pattern detection approach,”‘ Proc. 19,h Working Conf. on Reverse.
[10] 1. K. Jhans, V.K. Priya, “Improved analysis of re factoring in forked project to remove the bugs present in the system,” Internation Journal of Innovative Research in Science, Engineering and Technology, Vol.5, Issue. 2, February 2016.
[11] K. A M. Ferreira, M. A S. Bigonha, R. S. Bigonha, 1. F. O. Mendes, H. C. Almeida, “Idetifying thresholds for object-oriented software metrics,” The Journal ofSystems and Software, vol. 85, pp. 244-257, 2012.
[12] F. Palomba, G. Bavota, R. Oliveto, A de Lucia, “Antipattern detection: Methods, Challenges, and Open Issues,” Advances in Computes, pp. 201-238,2015.
[13] R. Oliveto, F. Khomh, G. Antoniol and Y. Gueheneuc, “Numerical signatures of antipatterns: An approach based on b-splines,” 141h European Conference on Software Maintenenance and Rengineering (CSMR), IEEE, 2010, pp. 248-251.
[14] M. Kessentini, H. Sahraoui, M. Boukadoum, and M. Wimmer, “Search based design defects detection by example,” ser. Lecture N otes in Computer Science, Berling 1 Heidelberg: Springer, 2011, vol. 6603, pp. 401-415.
[15] F. Khomh, S. Vaucher, Y. Guhneuc, and H. Sahraoui, “Bdtext: A gqmbased bayesian approach for the detection of antipatterns,”‘ Journal of Systems and Software, vol. 84, no. 4, pp. 559-572, 2011.
[16] D. Spinellis, “Tool writing: A forgotten art?,” IEEE Software, 22(4):9- 11, July/August 2005.
[17] A Rao, K. N. Reddy, “Detecting bad smells in object oriented design using design change propagation probability matrix,” Proceedings of the International MultiConference of Engineers and Computer Scientists, 2008.
[18] K. Dhambri, H. Sahraoui, P. Poulin, “Visual detection of design anomalies,”‘ Proceedings of the 12,h European Conference on Software Maintenance and Reengineering, IEEE Computer Society, pp. 279-283, 2008.
[19] M. 1. Munro, “Product metrics for automatic identification of bad smell design problems in Java source-code,” Proceedings of the 11 1h International Software Metrics Symposium, IEEE Computer Society Press, pp. 15, 2005.
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removalRelated Services
Our academic writing and marking services can help you!

Freelance Writing Jobs
Looking for a flexible role?
Do you have a 2:1 degree or higher?
Study Resources
Free resources to assist you with your university studies!



